Breached Password Detection Should Be a Standard Feature in Every Authentication Solution
Every year again, the steadily increasing number of passwords exposed in data leaks is shocking. In many cases, in addition to the password also the respective username or e-mail address and hence the combined login credentials are compromised and lead to an even larger and more widespread threat. The consequences range from simple identity theft to financial losses.
Hundreds of millions or even billions of accounts are revealed when sites or apps become targets. Increasingly sophisticated cyberattacks, Brute-Force-, Spraying- and Dictionary attacks, phishing attempts, and social engineering campaigns form today the gateway for hacker attacks and have been responsible for many security breaches that have taken place in recent years. Especially administrative and high-level accounts are popular targets for hackers.
Leaked passwords often end up for sale on the dark web. Hacking tools automatically try to steal personal information from databases. Consequently, leaked user accounts and gained login credentials can lead to all sorts of illegal operations like fraud and theft.
As a result of these attacks there is an ever greater need to secure the data of your IT admins and end users. Due to the steadily increasing global cyber threat landscape, no Identity and Access Management solution without a standard built-in Leaked Password Detection should be commissioned. However, it is important that all parties develop an awareness of the real danger of a potential password compromise and are ready to respond effectively in terms of their own digital security.
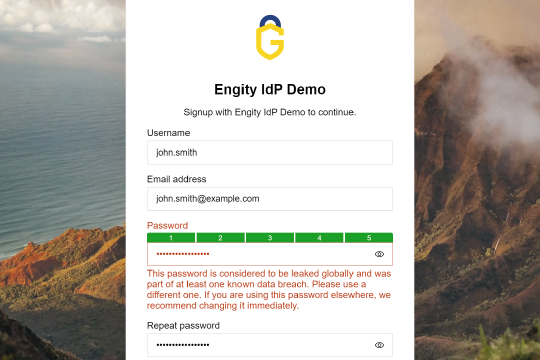
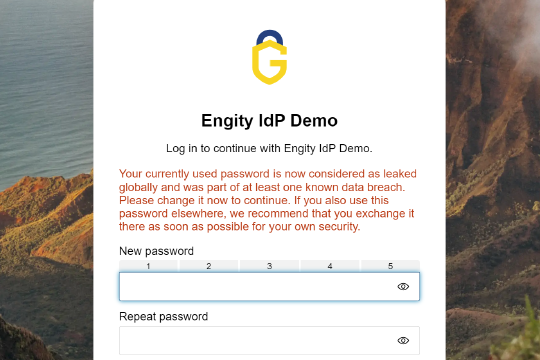
For Engity and its IAM solution, security is essential. That is why we offer the Breached Password Detection feature to all our customers by default. In addition to detecting leaked passwords, it is equally important to ensure that used passwords are strong and unique. For this reason, Engity also provides a password strength meter as a standard feature in its access solution.